When it comes to pentesting, the unavoidable topics are the terms like encryption, encoding, hashing and obfuscation. There is usually a lot of confusion when talking about these terms.
Let's take a closer look at each of these terms:
Encryption
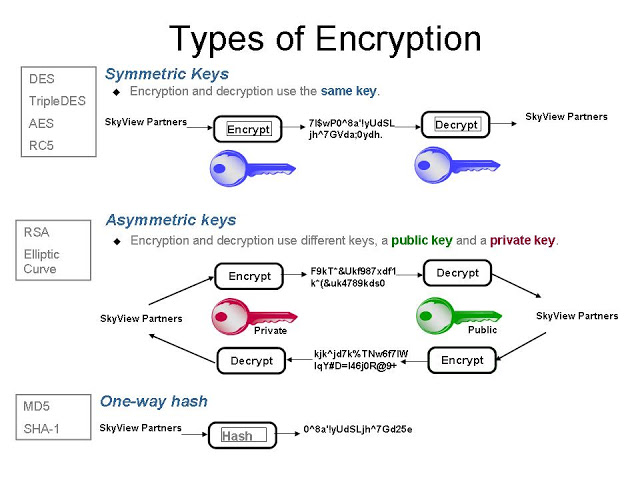
The purpose of the encryption is to transform and hide readable data (plaintext) by using an algorithm (cipher) to unreadable (ciphertext), e.g. if we send someone a message only to the person to whom the message is intended should be able to read it (decrypt it).
Encryption transforms plaintext data into a completely different value (ciphertext) in such way that only a specific person can return those data to the original value (plaintext). For that purpose, a secret key is needed, along with a plaintext and an algorithm in order to make the encryption. Then the encrypted text, the algorithm, and the key are needed to return the message to an original, readable form (plaintext). It is important to note that there is symmetric and asymmetric encryption.
Examples would be: AES, Blowfish, RSA
Encoding
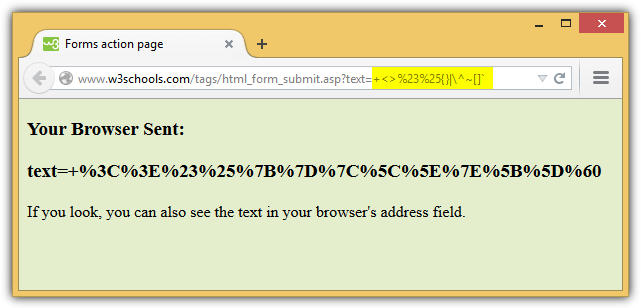
The purpose of the encoding is to transform data in a such way so it can be used correctly (and securely) by different systems, for example to send a binary information via an email or to review special characters (like č,ć,ž,đ,š) on the website or on the URL of the web page. The purpose of encryption is not to make an information a secret, but to use the information properly.
Encoding is used to convert data by using a publicly available scheme to different value and to retrieve that data again in its original form easily. For the encoding, any kind of key is not needed, only required thing is the decoding algorithm that was used to encode the data in first place.
Examples would be: ASCII, Unicode, URL Encoding, Base64
Hashing
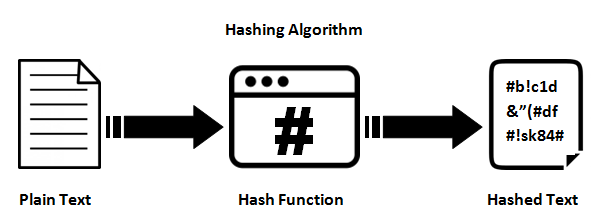
Hashing is used to ensure integrity. Hashing takes an arbitrary value, and gives at the output a string of the exact length with the following attributes:
- The same input value always gives the same output value.
- Different input values should give different output values.
- It should not be possible to return the output value to the original (input) value.
- Any change in the input value should give a completely different output result (hash).
Hashing examples: SHA1, SHA256, SHA-3, MD5 (obsolete) and so on.
Obfuscation
Obfuscation is used when there is a need to make something difficult to understand. It is often used to make the target harder to attack or to make it more difficult for someone to copy someone elses code. One use may be to make the source code of the application difficult to replicate if the reverse engineering is performed.
It should be noted that obfuscation is not encryption, but it is only an obstacle. As with coding, it is possible to get the original value by reversing.
Obfuscation carries other problems. If an obfuscation is applied to code, it must be applied to the code in extent that it makes code remain usable, otherwise the application will not work properly.
My example of an IP address obfuscator: https://www.ramicomer.com/en/blog/hide-obfuscate-ip-address-in-plain-text-with-obfuscated-equivalent/
Conclusion:
- Encryption is used to protect confidential data. To get an original message (plaintext) again, a secret key is needed.
- Encoding is a form of data transformation, the original value can be returned easily by using the same algorithm that was used to transform data in first place.
- Hashing serves to check the integrity of the content, it's almost impossible to get the original value.
- Obfuscation is used to prevent people from understanding something and the most common use is to prevent theft of product.